The Era of Agentic Commerce: A Strategic…

There is a new variable that needs to be considered in PE valuation: the impact of an undisclosed cyber breach. The deal team is constrained by three interrelated limitations when it comes to assessing cyber risk for a target: a lack of time, information asymmetry, and skill set.

Cybercrime may feel new, but human nature is timeless. Alarmingly, the FBI has reported a 300% increase in cybercrime since the outbreak of COVID-19[1]. Fraud, theft, deception, infiltration, ransom... despite innovation, at its core, cyber is a people problem, not just a technology problem. To understand cybersecurity, you must think like a criminal. In the film “Catch Me if You Can” the main character, Frank Abagnale, seems to share the same opinion. Whether Frank actually committed all the fraudulent schemes he claimed remains open to debate. But one maxim pointed out by Abagnale remains true regarding brazen exploits: “every breach occurs because somebody in that company did something that they weren’t supposed to do, or somebody in that company failed to do something they were supposed to do.”[2] Indeed, with respect to cyber incidents, four out of five breaches occur via an employee. One of the most common tactics includes social engineering which exploits human vulnerabilities.
Traditionally, during the due diligence process, private equity (PE) professionals focused primarily on the growth potential of the target. This emphasis is obvious. But there is a new variable that needs to be considered in valuation: the impact of an undisclosed cyber breach. The deal team is constrained by three interrelated limitations when it comes to assessing cyber risk for a target: a lack of time, information asymmetry, and skill set. And on top of that, according to IBM’s "Cost of a Data Breach Report", the 2020 average cost of a data breach in the United States is approximately $8.64 million.[3] The following cases regarding the Marriott and Yahoo transactions will highlight that Private Equity firms will increasingly need to integrate targeted cybersecurity assessments which may discover flaws or issues, not exploited but present. Thus, avoiding “buying the breach” resulting in net value destruction for the acquirer. Both the PE and cybersecurity space move at an incredibly rapid pace, increasing the pressure on deal teams in the near future...
In 2016, hospitality giant Marriott acquired Starwood Hotels, a high-profile merger that symbolized rapid growth in the travel industry. Two years later, disaster struck: it was discovered that over 500 million sensitive customer records had been stolen from the Starwood Hotels’ legacy database during the past four years, a time encompassing both the pre-merger and post-merger period (!). A public relations disaster ensued, leading to reputational damage and a $130 million (£99 million) fine from a UK court. It later became clear that Starwood acknowledged that its systems possessed significant security flaws well before the merger occurred, taking little action to remediate deficiencies during that time.[4]
Verizon’s acquisition of Yahoo for $4.48 billion also highlights the need for targeted cyber assessments in transactions. The deal almost fell through over two data-breach events that came to light in the midst of negotiations. In the first breach, a hacker stole the personal data of at least 500 million users, including some unencrypted passwords and answers to security questions. Later, it was believed that the hackers were allegedly aligned with Russian intelligence. This hack was accompanied by the discovery of a larger hack that occurred a year earlier and affected 1 billion Yahoo users. The full impact of these breaches came to light in 2016 when Yahoo submitted a filing with the Securities and Exchange Commission (SEC). Verizon still believed that the deal was a strategic move, despite the growing cybersecurity concerns. They lowered their initial price by $350 million due to Yahoo’s reduced valuation, closing at $4.48 billion. To cover breach-related costs, the agreement was revised to state that Yahoo would pay half of government investigation costs and fully absorb shareholder lawsuits and SEC investigations due to their lack of cyber insurance.[5]
Indicators of Compromise: If Marriott and Verizon had integrated a targeted cyber assessment in the due diligence process, they may have identified the Indicators of Compromise (IoC) in Starwood’s or Yahoo's systems. An IoC is an object or activity that, when detected on a network or device, indicates a high probability of unauthorized access (i.e. malicious activity).
An IoC is a leading indicator of a potential breach in which a deal team could present management with 3 options:
Therefore, a cybersecurity due diligence team needs to integrate a rapid targeted assessment of the target to determine key vulnerabilities and search for IoCs.
One of the key challenges for a deal team is to obtain, assess, and analyze the right information in order to develop a theory and a comprehensive detection strategy under time pressure. Therefore, PE teams should consider the following approach:
Identifying a breach before executing a transaction is difficult, but well worth the effort given the adverse impact of “buying a breach.” Even if the cyber team does not find IoCs or a breach, they may nevertheless realize that certain areas require further investigation. If significant vulnerabilities are discovered during the due diligence process, companies can adjust their acquisition strategy and pricing.
To learn more how Sia Partners can help you enhance transaction due diligence by deploying a cyberbot Flash Audit, please refer to our solution summary below.
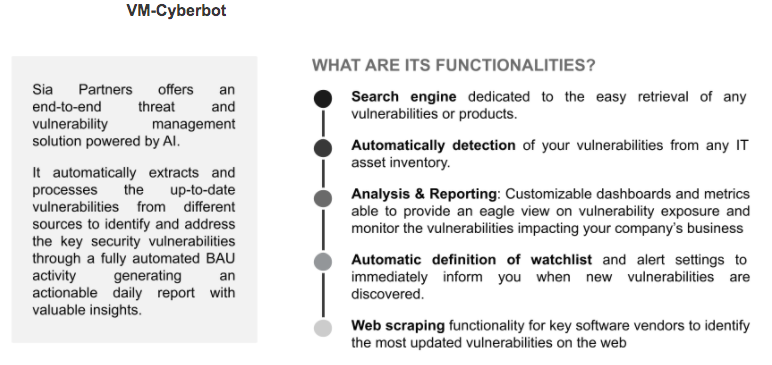
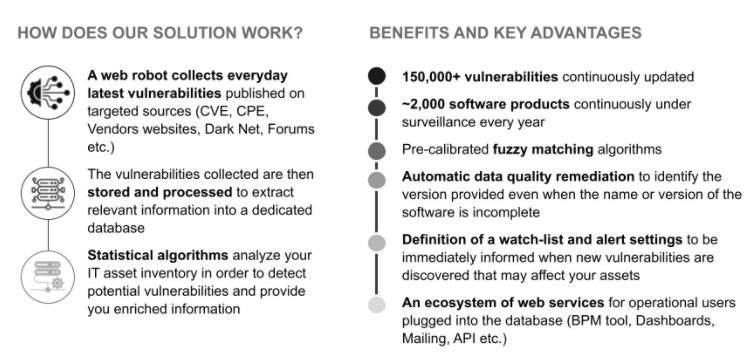
Sia Partners Data Science and Cyber Security experts have developed a light and fast solution that does not require any agent installation but uses existing inventory. Indeed, VM-Cyberbot can perform a Flash Audit of any IT Asset inventory to assess an organization's cyber vulnerabilities providing a complete and actionable summary of security status, over a specific scope and timeframe.
More concretely, the audit relies on pre-calibrated fuzzy matching algorithms that will analyze an already existing IT asset inventory even with poor data quality and identify the existing vulnerabilities in real-time – collected through our Web Scraping technologies. VM-Cyberbot produces a global report immediately. Our Cyber professionals use these results to define an overall level of risk in order to make recommendations.
Flash Audits are highly automated and require minimal resources. The transaction team simply needs to provide access to the IT asset inventory of the company. Crucially, the audit does not require access to the company assets or any other confidential information. Depending on the number of assets, it takes just a few days for Sia Partners experts to check the inventory, run the model, and produce the results.
Engagement Director, Cybersecurity, FRM, CISSP | New York
Chris has over 20 years’ experience in risk management covering the banking and insurance sectors as both a practitioner and consultant. Chris leads Sia Partner’s Cybersecurity and Data Privacy practice in the United States.

[1] FBI sees spike in cyber crime reports during coronavirus pandemic
[2] Think like a criminal to beat them at their own game — Frank Abagnale Jr
[3] Cost of a Data Breach Report 2023
[4] Marriott Announces Starwood Guest Reservation Database Security Incident
[5] Its official verizon finally buys Yahoo