Fortune 100 response to DE&I pressures

In response to the growing and escalating threat of global cyberattacks, Europe, China, and now Hong Kong have taken steps to enhance the cybersecurity of its critical infrastructure operators.

Hong Kong is establishing new legislation around critical infrastructure computer systems that will require organizations to meet organizational, preventive, and incident management obligations to a government body.
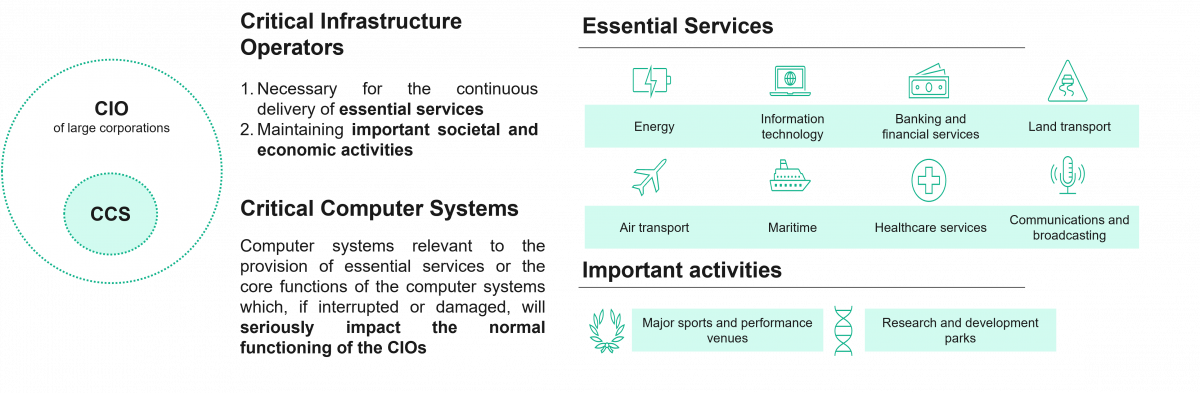
This new legislation, titled the 'Protection of Critical Infrastructure (Computer System) Bill', targets Critical Infrastructure Operators (CIOs) and Critical Computer Systems (CCS) of large organizations in Hong Kong.
The bill defines CIOs as infrastructures necessary for the continuous delivery of essential services or for maintaining important societal and economic activities in Hong Kong. Like European and China regulations, this local regulation covers essential services such as energy, information technology, banking and financial services, land transport, air transport, maritime, healthcare services, and communications and broadcasting. Regarding important societal and economic activities, it should cover major sports and performance venues and research and development parks.
This legislation has divided statutory obligations into three categories:
provide and maintain an address and office in Hong Kong (and report any subsequent changes);
report any changes in the ownership and operations of their CI to the Commissioner’s Office;
set up a computer system security management unit, supervised by a dedicated supervisor of the CIO.
inform the Commissioner’s Office of any material changes to their CCS, including changes to design, configuration, security, operation, etc;
formulate and implement a computer system security management plan and submit the plan to the Commissioner’s Office;
conduct a computer system security risk assessment (at least once every year) and submit the report;
conduct a computer system security audit (at least once every two years) and submit the report;
adopt measures to ensure that third-party service providers are compliant with the relevant statutory obligations.
participate in a computer system security drill organized by the Commissioner’s Office (at least once every two years);
formulate an emergency response plan and submit the plan;
notify the Commissioner’s Office of the occurrence of CSS security incidents within 24 hours and 2 hours for serious incidents after becoming aware.
All changes in the address, ownership, or material shall be reported within 30 days.
This new legislation empowers a dedicated government office, the Commissioner’s Office, to monitor compliance with cybersecurity obligations. The Commissioner’s Office will have the authority to levy fines for non-compliance, ranging from HK$500,000 to HK$5 million (approximately US$64,000 to US$640,000). Additionally, the office can impose daily fines of HK$50,000 or HK$100,000 for persistent offenses. It’s important to note that these offenses and penalties are not applicable at the individual level, except in cases where the violations also constitute violations of existing criminal laws.
More details on the obligations are defined in Annex III of the proposed legislation and the Hong Kong government FAQ.
According to information provided by the government, the new cybersecurity regulation is expected to take effect in early 2026. CIOs will have a six-month compliance period to meet the requirements.
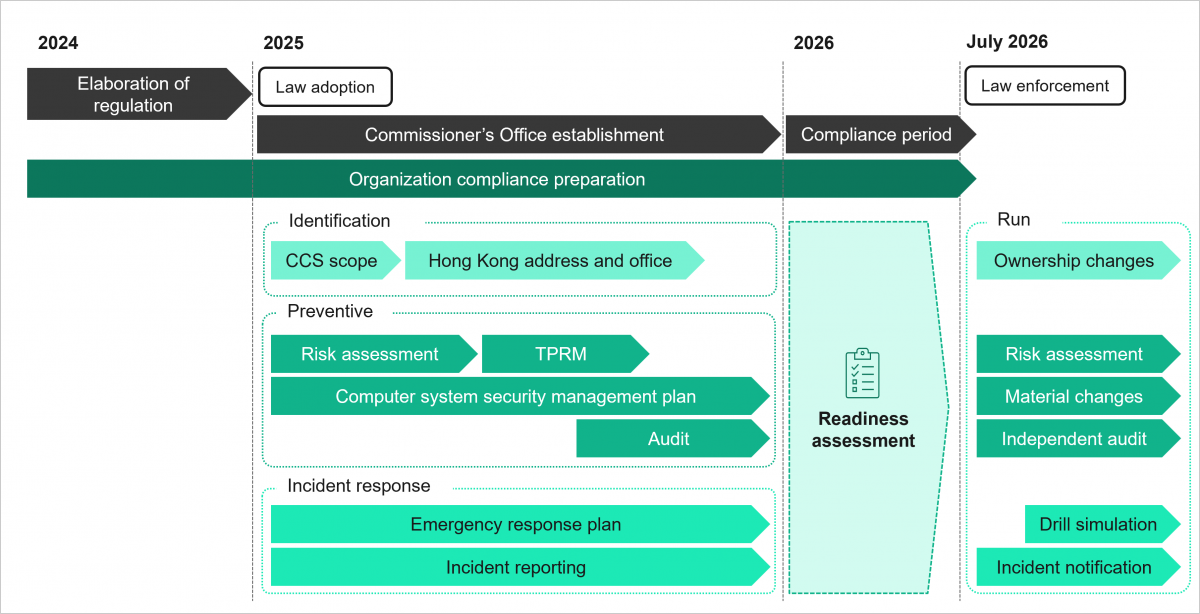
In the lead-up to the new regulation taking effect, organizations can take the following steps to prepare for compliance:
Assess your potential status as critical infrastructure operators (CIOs) and identify your critical computer systems by leveraging asset management, for example.
Sia Partners has extensive experience helping its clients identify and assess regulatory perimeters and define critical systems.
Evaluate your current maturity level against the "Code of Practice" outlined in Annex III of the proposed legislation and elaborate a remediation plan.
Our experts provide highly detailed and risk-based maturity level analyses that will propel organizations beyond regulatory compliance.
Review your third-party risk management process and update existing and future third-party contracts to ensure they align with new obligations, if needed.
Sia Partners specializes in third-party management processes and believes that it is crucial to ensure security throughout the entire supply chain. Our methodology is based on internationally recognized standards such as NIST CSF, ISO 27001, and others.
Enhance your incident management and emergency response plans to ensure the correct qualification of the incidents, and notification within 2 hours when applicable. Thanks to our comprehensive crisis management and continuity plan offerings, Sia Partners serves as your dedicated partner in preparing for potential attacks. Our services encompass tabletop exercises designed to simulate your reactions and assess your overall level of readiness.
Update your overall risk analysis. This regulation presents an opportunity to improve your risk and cybersecurity posture. Our risk management methodology assists your organization in implementing a comprehensive approach to risk which ensures a sustainable business.
The list of organizations covered under the new cybersecurity regulation will not be publicly disclosed, due to concerns about these entities becoming targets of terrorist attacks. However, the designated Critical Infrastructure Operators (CIOs) will receive direct notifications.
Even for CIOs that have been notified, there is still a need to clearly define the scope of "Critical Computer Systems" (CCS) that fall under the regulation. Determining what qualifies as a critical system, and to what extent a component is considered critical, could be a complex undertaking. This is because the criticality of a system or component may depend on factors such as its role, the availability of alternatives, and the potential impact of disruption.
The proposed legislation requires CIOs to ensure compliance, not just for their systems, but also their third-party service providers that fall within the CCS scope. In other words, CIOs are responsible for verifying that their contractors and vendors meet the required security standards, even though the third-party providers are not directly regulated under the new law. Inspired by the fourth pillar of the European regulation on the Digital Operational Resilience Act (DORA), organizations should list all third-party providers, review their evaluation and update contracts if necessary.
Defining what constitutes a "major incident" that warrants a 2-hour notification will be crucial, as it may involve complex forensic analysis within a tight timeframe. The regulation seems to refer to an incident with a significant impact on the continuity of essential services and the normal functions of CIs, or one that leads to a large-scale leakage of personal information and other data.
Banks and other financial institutions in Hong Kong are already subject to cybersecurity regulations imposed by the Hong Kong Monetary Authority (HKMA). With the introduction of this new cybersecurity legislation, jurisdictional responsibilities will overlap between the HKMA and the new Commissioner's Office.
To minimize this overlap and alleviate concerns, the government has decided on a two-pronged approach:
As the Primary Regulator for organizational and preventive pillars, the HKMA will oversee organizational and preventive cybersecurity obligations in the banking and financial services sector for CIOs regulated by the HKMA.
A Unified Reporting Channel for incident reporting and response pillar: The Commissioner's Office will still be responsible for incident reporting and response obligations. To address this, the government has indicated that a unified reporting channel and compliance regime can be established. This would allow financial institutions to fulfill their incident reporting requirements through a single, streamlined process - reporting to both the HKMA and the Commissioner's Office.
The Hong Kong government has explicitly stated that the formulation of this new regulatory regime has taken international cybersecurity practices and standards into account, especially the EU's NIS 2 directive. However, it's important to note that the Hong Kong and China's mainland legislation (Cybersecurity Law 2016 and Regulation for Safe Protection of Critical Information Infrastructure 2021) each have their own distinct scopes and requirements. This means that regional or international companies operating in both Hong Kong and China's mainland will need to carefully identify and define which of their systems fall under the respective jurisdictions.
Hong Kong's cybersecurity law is prescriptive, with specific requirements enforced by the government, while the NIS 2 Directive adopts a flexible, risk-based approach, allowing entities to tailor measures to their assessed risks.
NIS 2 is part of a broader EU strategy to enhance cybersecurity across multiple sectors and borders, whereas the Hong Kong law is more localized, focusing on specific sectors within the city.
Closer to Hong Kong, Singapore has also followed suit by amending its Cybersecurity Act. In May 2024, Singapore’s Parliament passed an Amendment proposed by the Cyber Security Agency of Singapore (CSA) to expand the oversight of the CSA, focusing on enhancing the resilience of Singapore’s critical information infrastructure (CII). The aim is to keep pace with developments in the cyber threat landscape and the evolving technological operating environment.
Sia Partners brings unparalleled expertise in cybersecurity, compliance, and risk management from a global network of markets, empowering clients in Hong Kong to elevate their compliance and cybersecurity maturity to new heights.
As an international firm with extensive experience in cybersecurity and resilience management for critical infrastructure sectors globally, Sia Partners is well-positioned to assist organizations in navigating the complex compliance landscape created by this new cybersecurity regulation.