Fortune 100 response to DE&I pressures

Every year, SWIFT updates and publishes security controls that all SWIFT users must apply to their SWIFT-related infrastructure. This article will highlight updates to the annual assessment and attestation process and provide best practices and strategies for CISOs to consider in the 2022 update.

SWIFT is the world’s largest provider of secure financial messaging services to banks and other financial institutions. The network has more than 11,000 users in over 200 countries, which makes it an attractive target to cybercriminals looking for banking information to perpetuate their fraudulent schemes.
Since the 2016 cyber-heist against the Central Bank of Bangladesh that resulted in a loss of $81 million, SWIFT introduced a common set of security controls to foster a more secure financial ecosystem. The Customer Security Programme (CSP) is an industry cooperative to reinforce and safeguard the security of information sharing within the entire ecosystem. As part of an effort to enhance the cybersecurity of the entire ecosystem, members of SWIFT were required to annually self-attest to an initial set of mandatory cybersecurity controls.
Even with enhanced measures for security, it appears that SWIFT cyber fraud, with increasing levels of sophistication, has been on the rise since 2016. Banks and financial services providers cannot risk taking a hands-off approach by relying on the SWIFT network to prevent any fraud. The annual assessment process gives firms the opportunity to not only ensure compliance with SWIFT standards but also be proactive in strengthening current security measures.
SWIFT users will need to support their attestation against 2021 standards with an independent internal or external assessment to submit by the end of the year. SWIFT has also published CSCF v2022 for attestation due December 2022 that can also be kept in mind this year.
The CSP establishes a common set of security controls, the Customer Security Controls Framework (CSCF), to help users secure their systems.
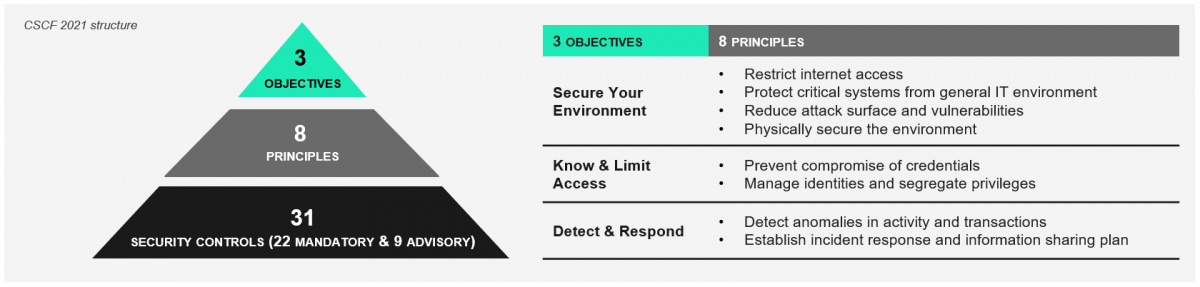
All controls are articulated around three overarching objectives, which is underpinned by eight principles. SWIFT developed the controls to mitigate cybersecurity risks by analyzing their cyber threat intelligence and feedback from industry experts and users. These controls are constantly evolving to keep up with cybersecurity practices or for any changes in technologies and regulatory modifications. SWIFT reports any non-compliant organizations to industry regulators.
Each year, users must have their security controls reviewed by an independent party as an informative assessment that will help fill out the annual self-attestation. SWIFT considers mandatory controls as realistic goals for near-term implementation, tangible security gain and risk reduction. Advisory controls are based on good practice that SWIFT recommends users implement. Over time, mandatory controls may change while some advisory controls may become mandatory.
SWIFT had announced that the assessment required for the year 2020 will be based on the 2019 benchmark. The requirements initially planned are postponed for one year, in addition to the new requirements introduced in 2021.
These requirements are of major importance to SWIFT users: in the event of non-compliance with the new control framework, SWIFT could report misconduct to the local supervisory authority and notify users of the SWIFT network.
The CSCF v2021 builds incrementally on last year’s version, as SWIFT minimized the number of changes to ensure the community has more time to fully implement the controls from previous CSCF versions. For 2021, SWIFT:
Since the CSCF v2020 controls were rolled into CSCF v2021, users will need to attest against that framework in the second half of 2021 with an independent internal or external assessment.
Recently, SWIFT published a new version of the CSCF for users to attest against in the second half of 2022. In addition to updated security controls, SWIFT established a new CSCF Working Group of 23 National Member and User Groups to centralize, prioritize, and review all feedback from the community before finalizing the recommended changes.
The updated security controls include:
Sia Partners is listed as a cyber security provider and an assessment provider in SWIFT directories to support the Customer Security Programme (CSP).*
We have worked on numerous engagements relating to CSP and our consultants have in-depth knowledge in supporting the client in preparing the SWIFT CSP attestation. From our experience conducting SWIFT assessments, these are ten points that we recommend CISOs be particularly mindful of in consideration of the v2021 (and future) updates.
Sia Partners is one of the few consulting firms to be globally recognized as a SWIFT cyber service provider and auditor.
Our global consultancy practice can assist with SWIFT CSCF review, compliance with privacy laws in multiple jurisdictions, and integration of the latest cybersecurity tools into your daily workflow. As emphasized by SWIFT, compliance to control objectives is a risk-based approach: while mandatory controls are prioritized for near-term tangible risk reduction, advisory controls are based on recommended best practices for all users.
Sia Partners has extensive experience helping organizations enact best practices in cybersecurity. Our market-leading expertise in Cyber Risk Management and Data Privacy can help your organization stand up an information security program that fits your needs.
Sia Partners can assist SWIFT users in evaluating the maturity of their current cybersecurity framework, including processes, controls and governance. Our objective is to design the most efficient controls to close the gaps with the targeted framework and help the organization in the implementation of controls.
*SWIFT does not certify, warrant, endorse or recommend any service provider listed in its directory and SWIFT customers are not required to use providers listed in the directory.